Notes on Lesson Plans
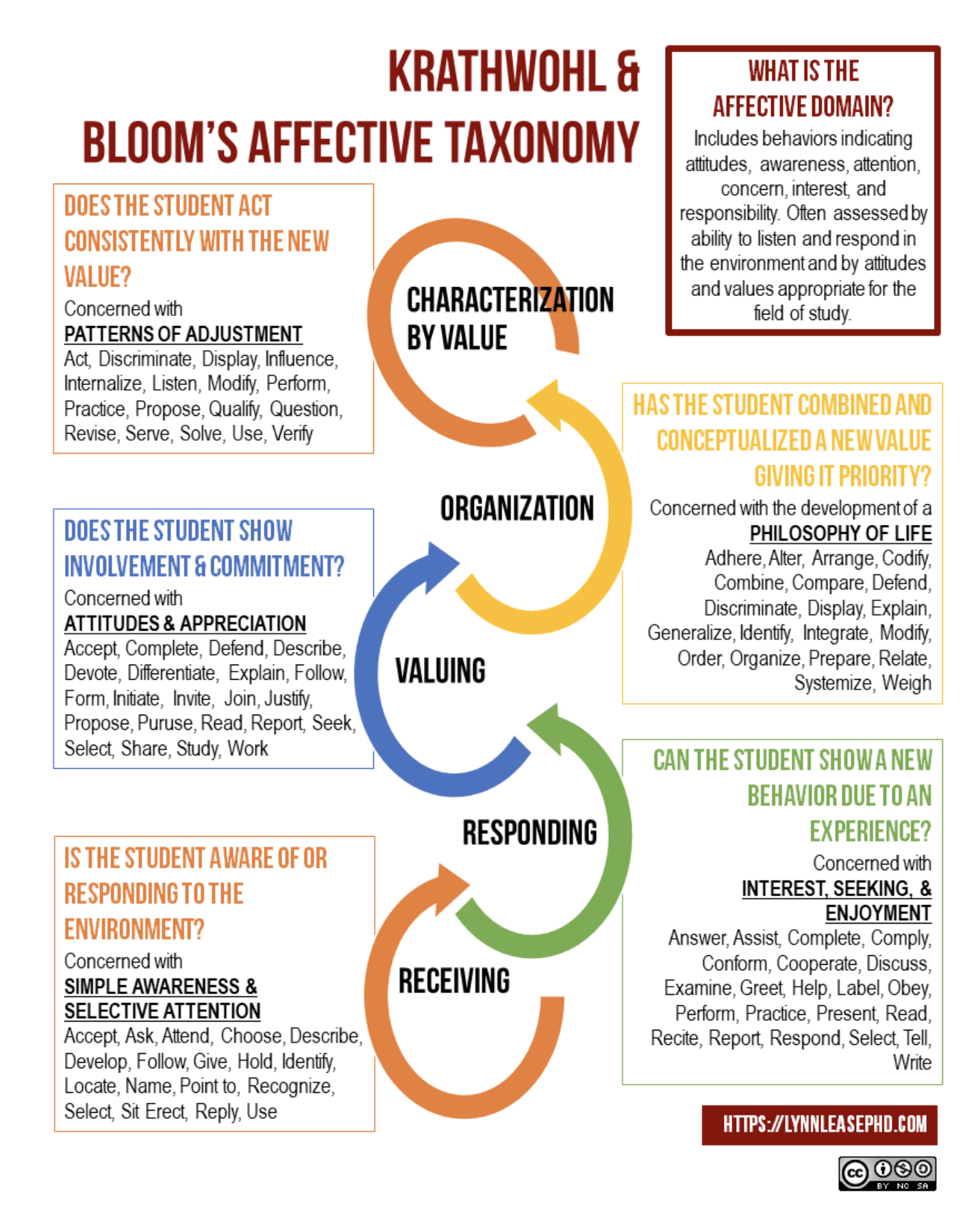
Bloom’s Taxonomy (Krathwohl, 2002) guides the intended progression of learning in each of these Cybersecurity 103 lessons, helping students move from awareness to action with confidence. Each lesson includes activities that lead with remembering and understanding. Students define key terms, explain the reasons behind cyber threats such as phishing, and explain how college students are targeted. The rest of the lesson scaffolds with application of knowledge, analytical thinking, and evaluation of options. Students exercise critical thinking as they identify examples and non-examples of phishing emails, and practice secure responses in the event of a compromised account. As the lessons progress, students analyze real scenarios and consider a range of response options, ethical responsibilities, and institutional reporting procedures. Bloom’s underlies NIST’s Cybersecurity Framework by aligning the cognitive and affective levels of learning with the Framework’s actions. By moving from the concrete, like rules to remember, toward more complex learning, like how to think and act in response to digital risks, this Cybersecurity 103 curriculum helps to prepare students to Protect, Detect, Respond, and Recover.
National Institute of Standards and Technology. (2024). The NIST Cybersecurity Framework (CSF) 2.0. NIST. https://nvlpubs.nist.gov/nistpubs/CSWP/NIST.CSWP.29.pdf